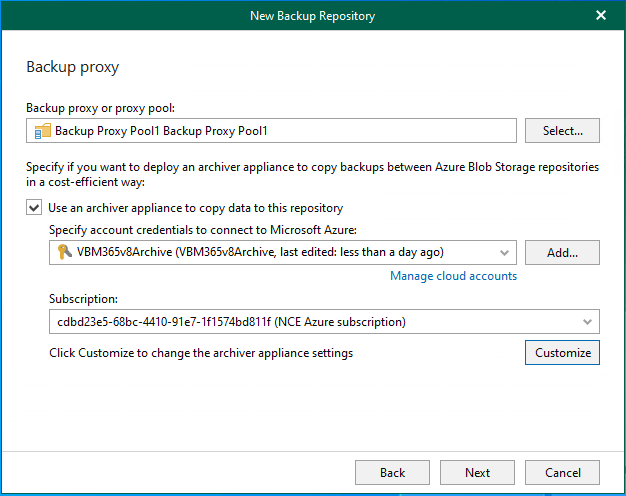
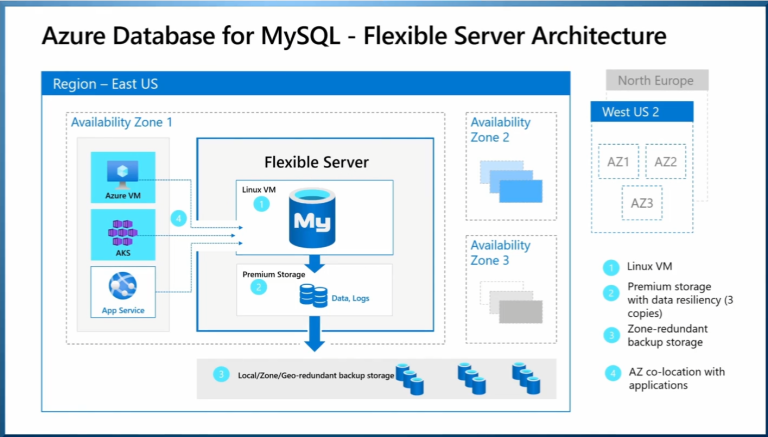
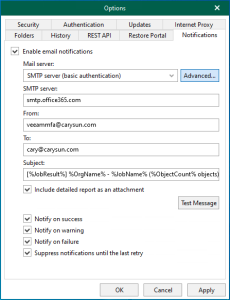
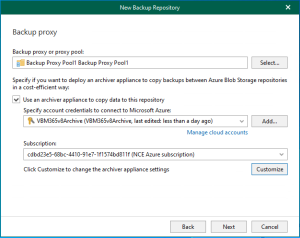
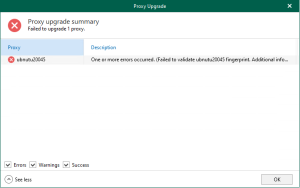
Veeam Backup for Microsoft 365 uses the Veeam Azure archiver appliance, a small virtual...
Azure
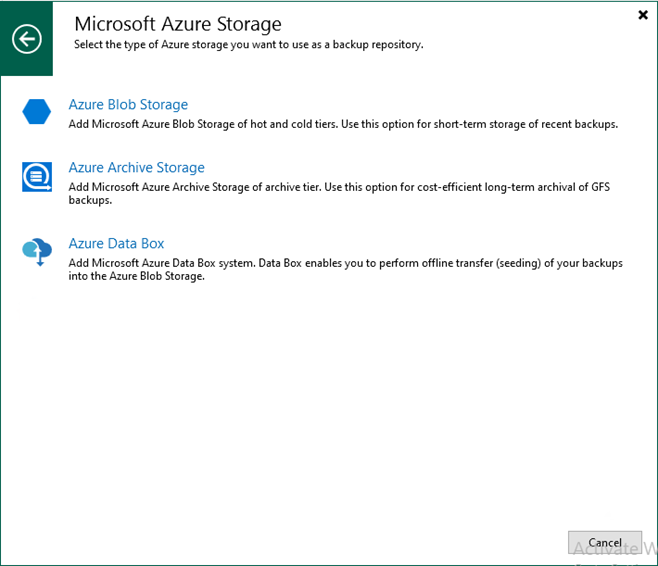
In Veeam Backup for Microsoft 365 version 8.2, adding a Microsoft Azure Archive Storage...
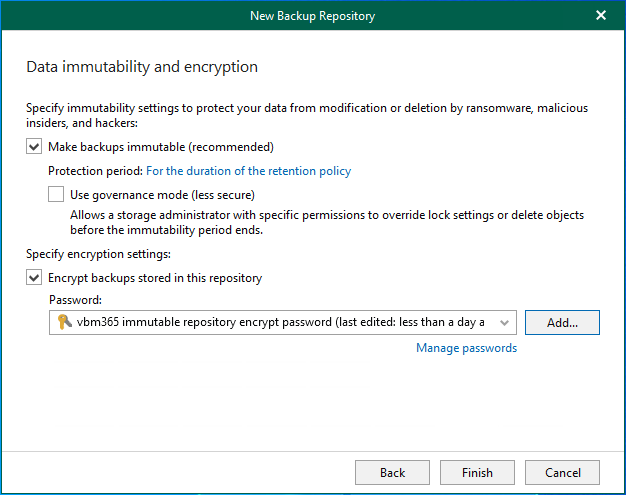
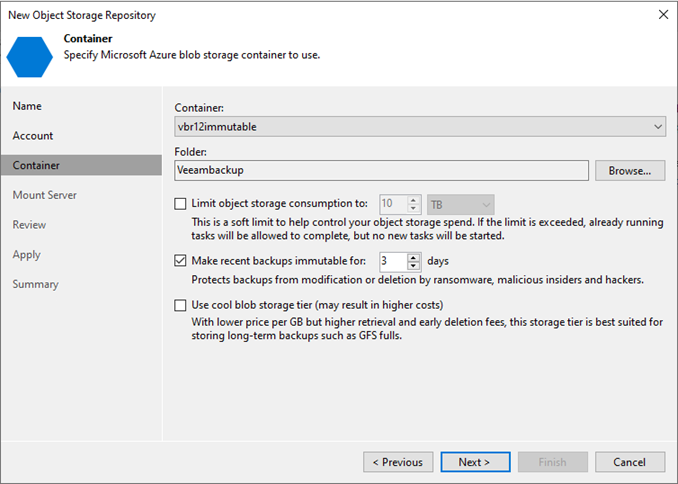
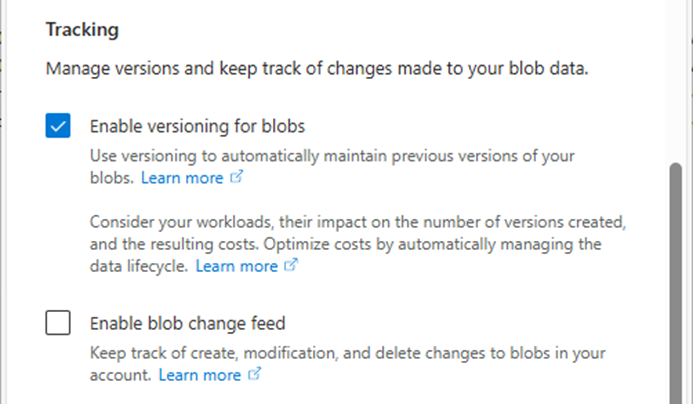
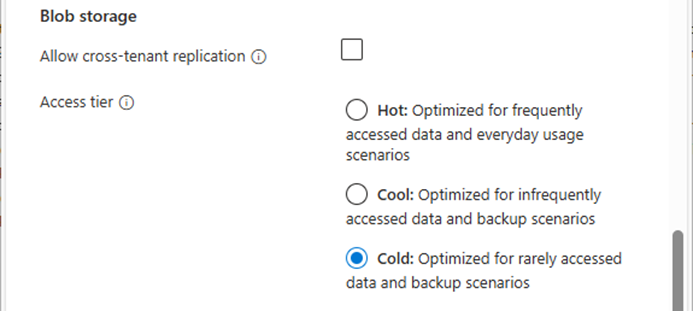
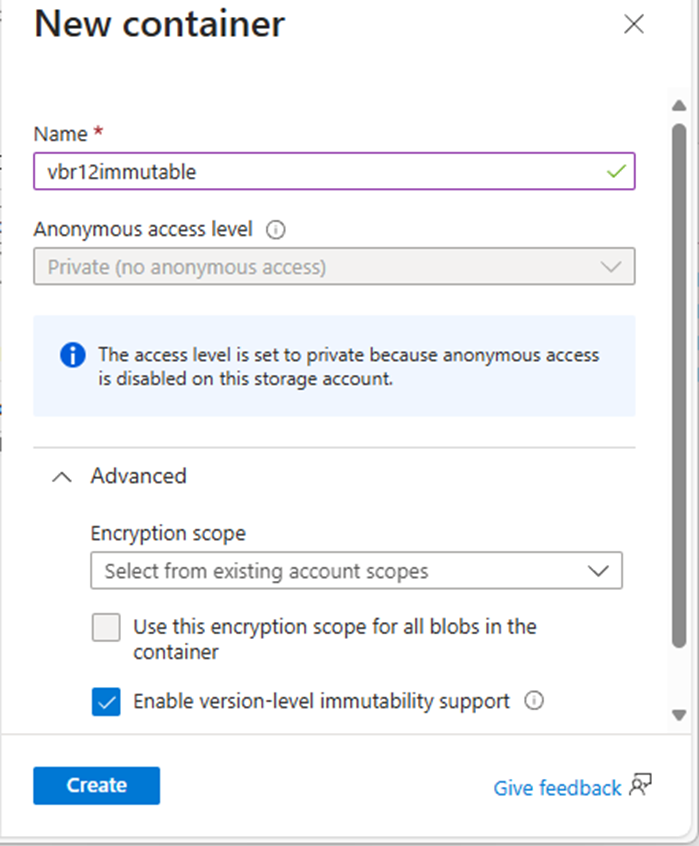
Integrating Microsoft Azure Blob Storage repositories with immutability requires configuring both the Azure storage...
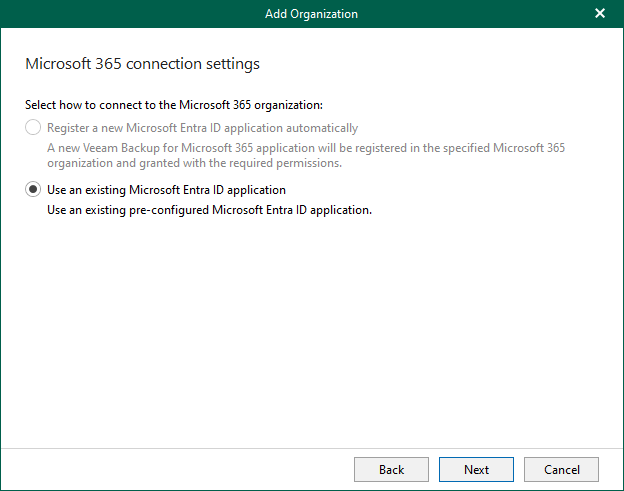
When you add an organization using the modern app-only authentication method, Veeam Backup for...
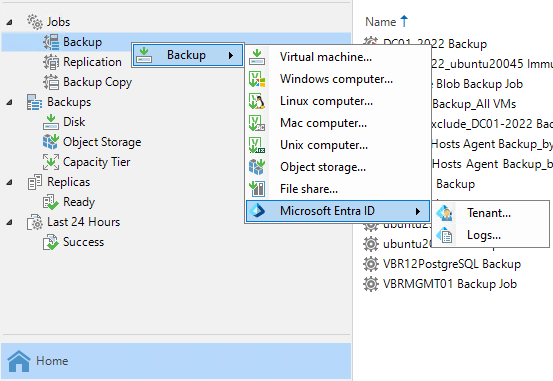
Veeam Backup for Microsoft Entra ID Logs to protect tenant audit and sign-in logs.
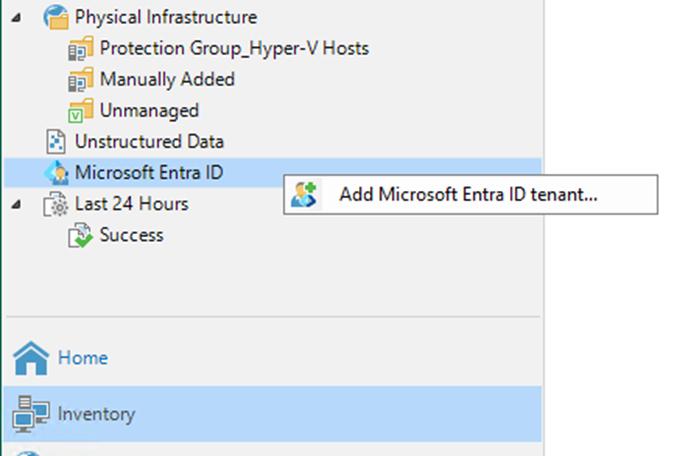
After you've added a Microsoft Entra ID tenant to the backup infrastructure, you can...
Beginning with version 12.3, the Veeam Backup & Replication solution allows you to add...
This section describes creating a backup copy job that off-loads to the Azure blob...
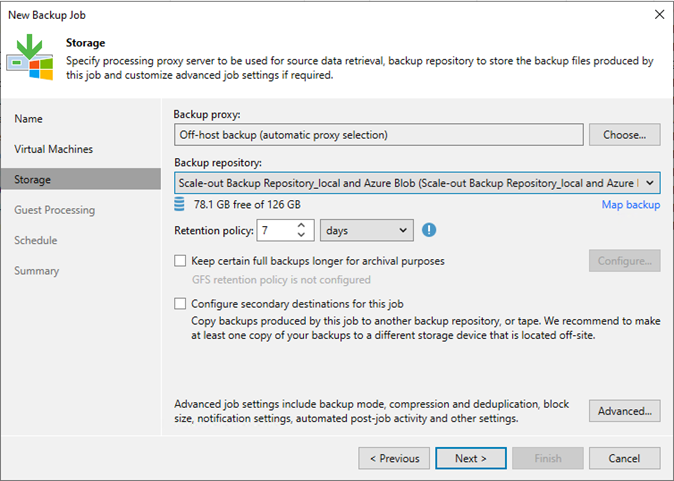
This section describes creating a backup job that backs up at local repositories to...
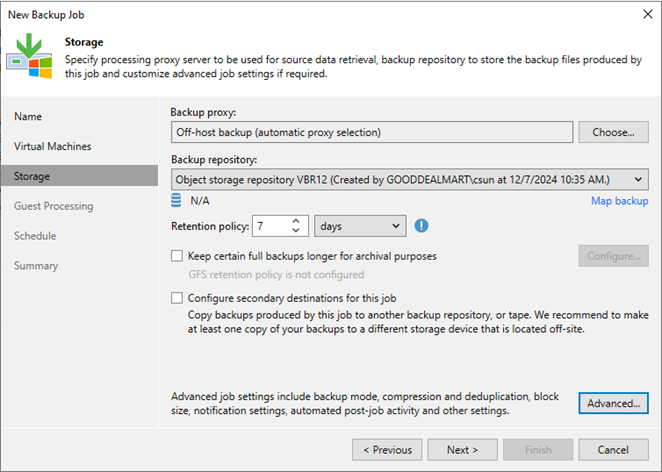
This procedure immediately creates a backup job to backup to Azure Blob Repository without...
This section describes how to add Azure Blob Object Storage Repositories as the performance...
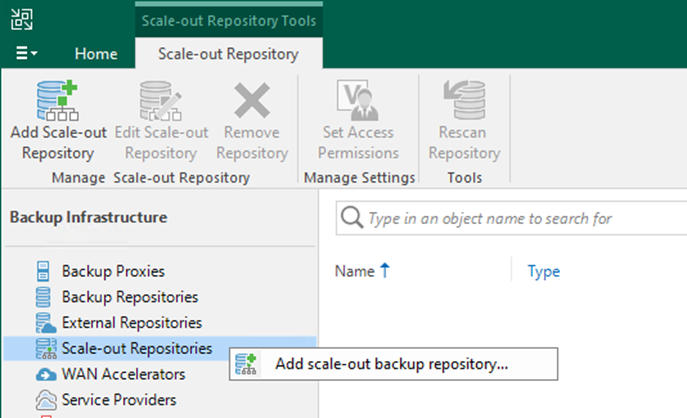
A scale-out backup repository allows for horizontal scaling for multi-tier data storage.
Veeam released a version of Veeam Backup for Microsoft 365 v8.1 on January 23,...
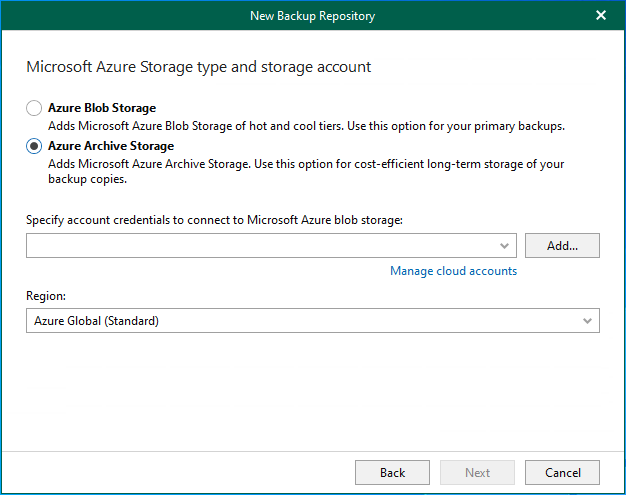
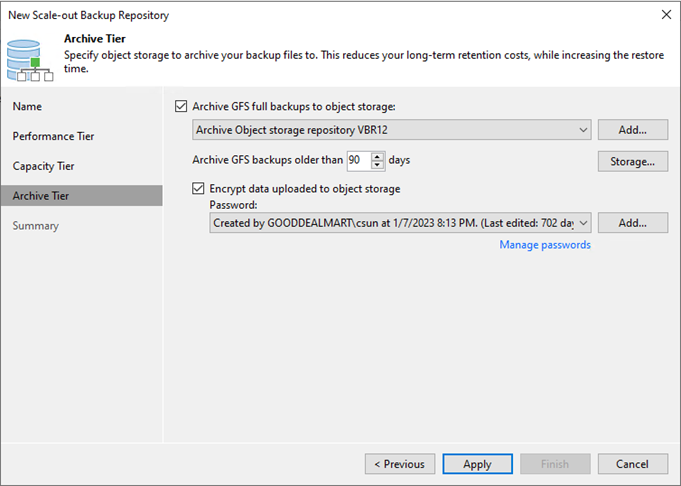
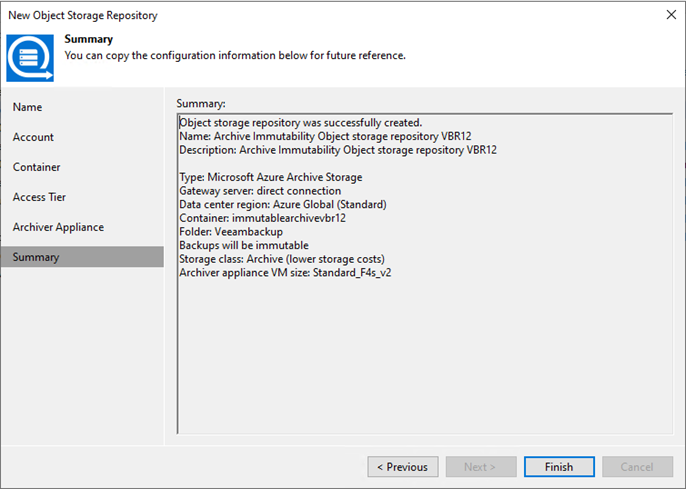
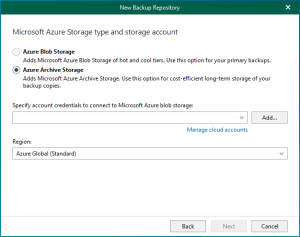
This section explains adding Microsoft Azure Archive Storage as an immutability archive backup repository...
These steps show how to add Microsoft Azure Archive Storage to the backup infrastructure...
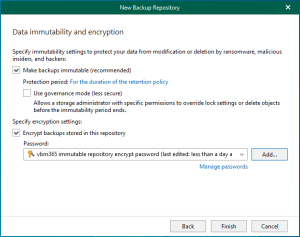
Veeam Backup & Replication allows you to prevent data deletion from the object storage...
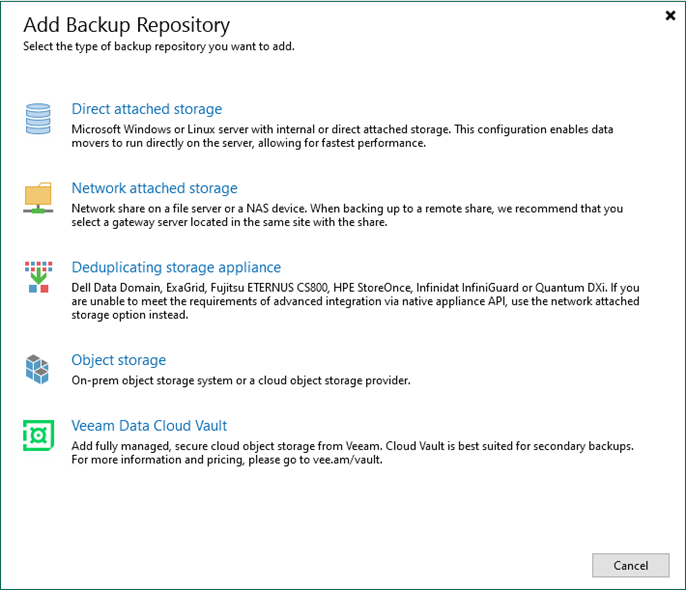
To add Microsoft Azure Blob Storage as an object repository without immutability, you normally...
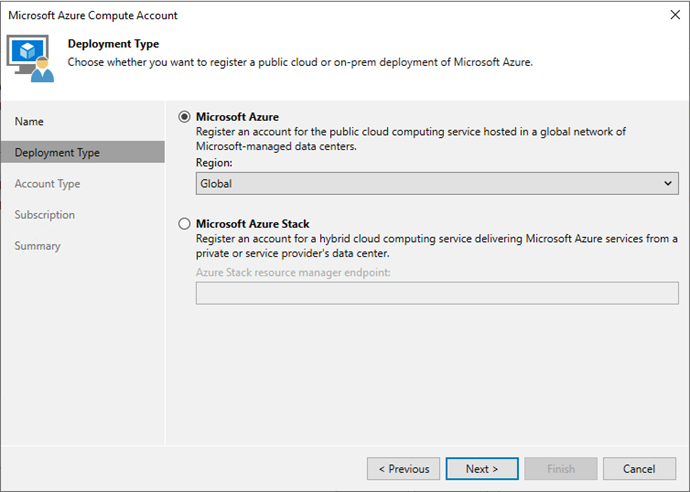
To add Microsoft Azure Compute Accounts to Veeam Backup & Replication (or Veeam Backup...
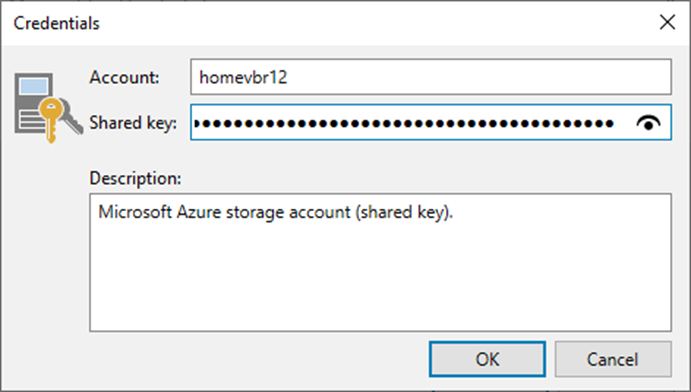
This Veeam cloud credential is for a Microsoft Azure Blob Object Storage Account with...
This Veeam cloud credential is for a Microsoft Azure Blob Object Storage Account with...
Veeam Backup & Replication allows you to prevent data deletion from the archive extent...
Azure Archive Storage is a low-cost, high-durability cloud storage tier inside Azure Blob Storage...
There are some immutability limits in the Azure Blob Storage.
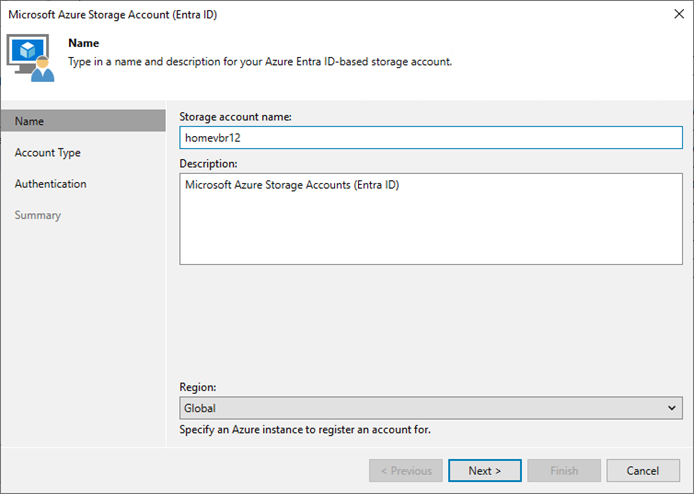
Veeam Backup&Replication supports different types of storage accounts.
There is good news if you are trying to build a WordPress website at...
Veeam released a version of Veeam Backup for Microsoft 365 v8 on September 11,...
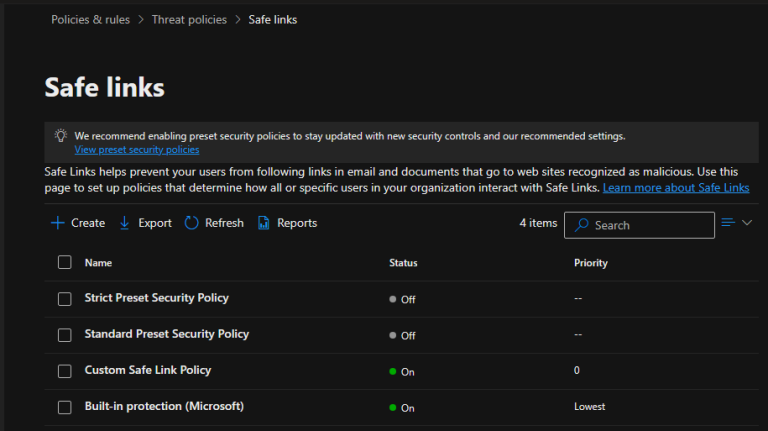
Safe Links is a feature in Microsoft Defender for Office 365 (formerly known as...
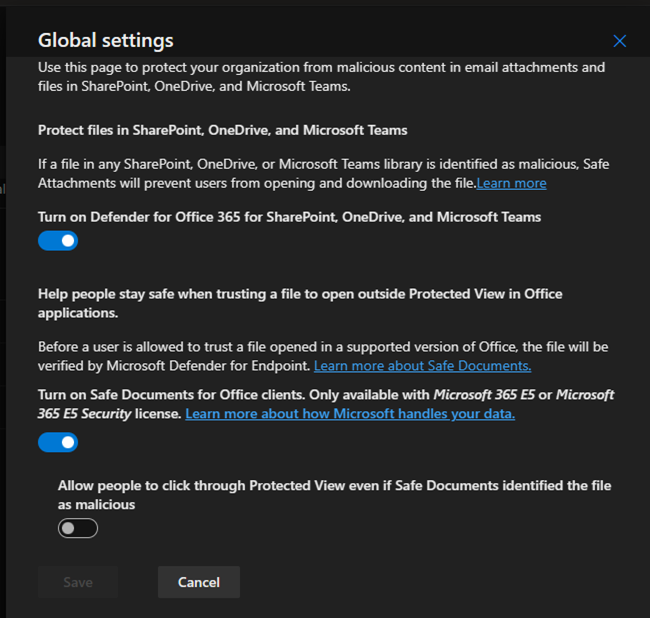
In Microsoft Defender for Office 365, Safe Attachments is a feature that helps protect...
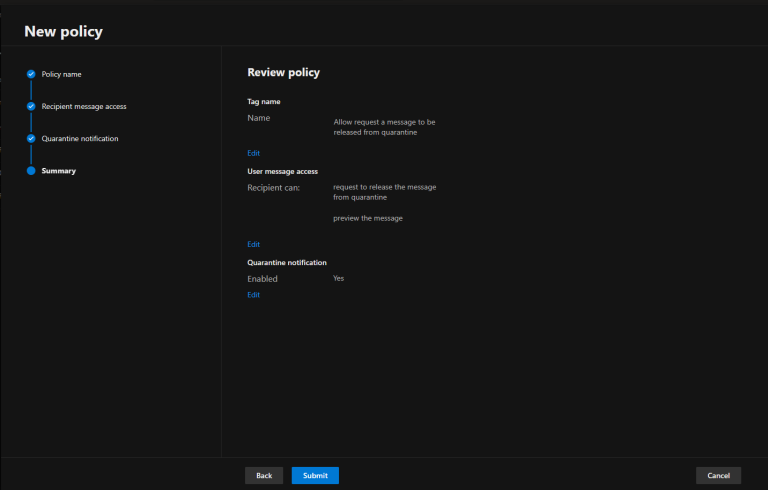
Creating a custom quarantine policy in Microsoft Defender for Office 365 involves configuring advanced...
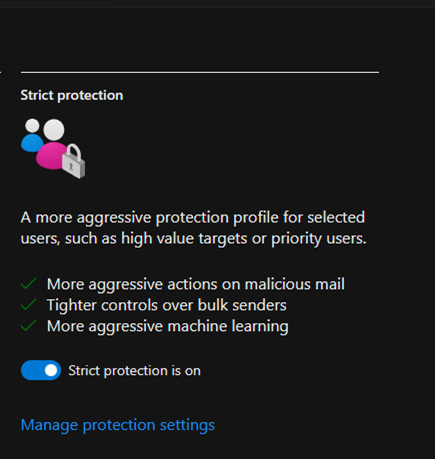
Strict preset security policies typically refer to predefined rules and guidelines designed to enhance...