You can back up and restore the On-Premises physical machines running Linux operating systems. Backup agents are installed on each computer by Veeam Backup & Replication.
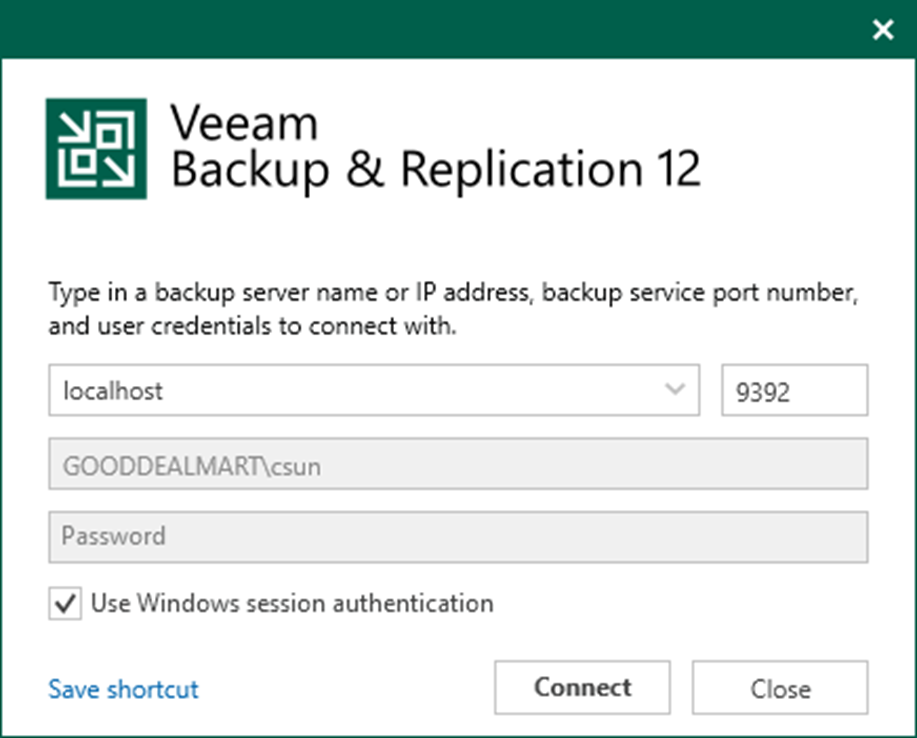
1. Login to the Veeam Backup and replication manager server.
2. Open the Veeam Backup & Replication Console and click Connect.
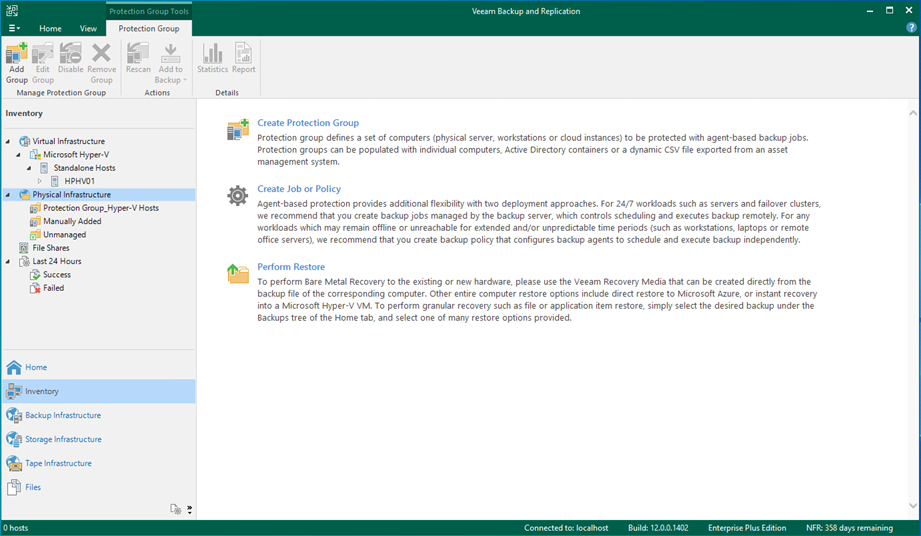
3. Select Inventory on the Home page.
4. On the Inventory page, select Physical Infrastructure and click Create Protection Group.
5. On the Name page, specify a protection group name.
6. Give a brief description in the Description field for future reference and click Next.
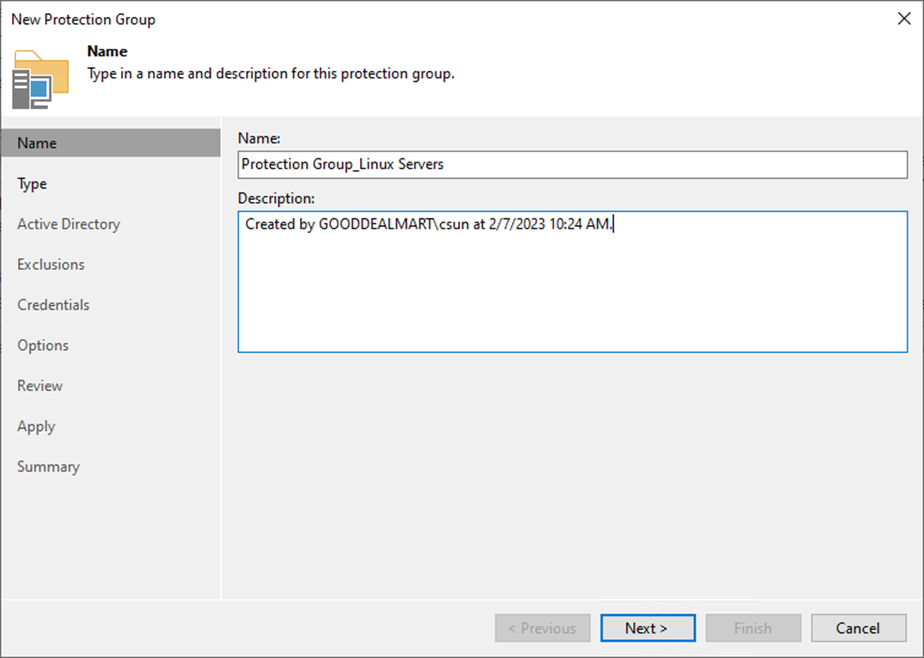
7. Select Specify protection scope for the created protection group on the Type page and click Next.
- Individual computers: add specific computers to the protection group.
- Microsoft Active Directory objects: select this option to add one or several Active Directory objects to the protection group.
- Computers from CSV file: add to the protection scope computers listed in a CSV file.
- Computers with pre-installed agents: create a protection group for pre-installed Veeam Agents.
- Cloud machines: select this option to add Amazon EC2 instances or Microsoft Azure virtual machines.
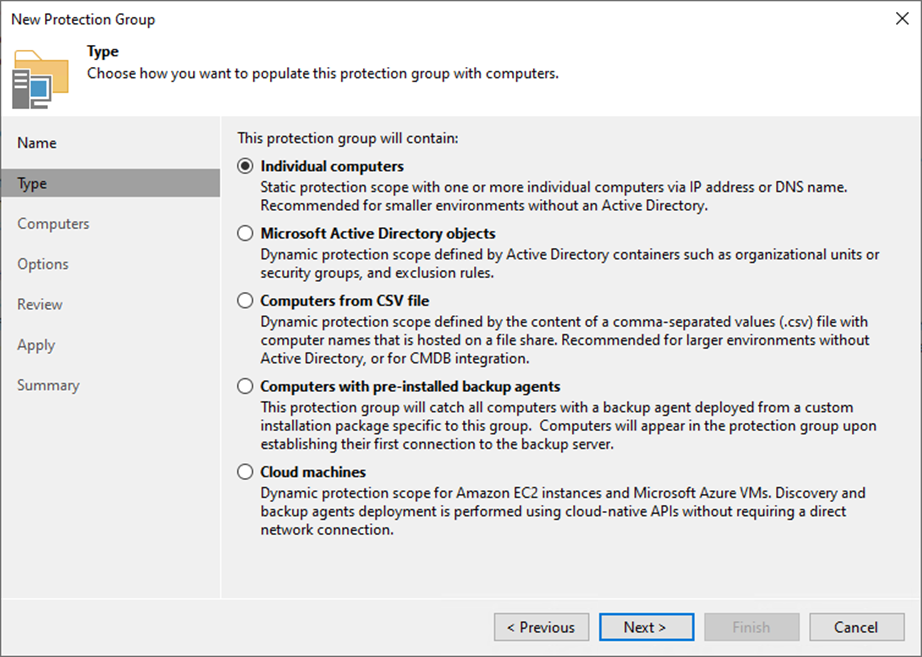
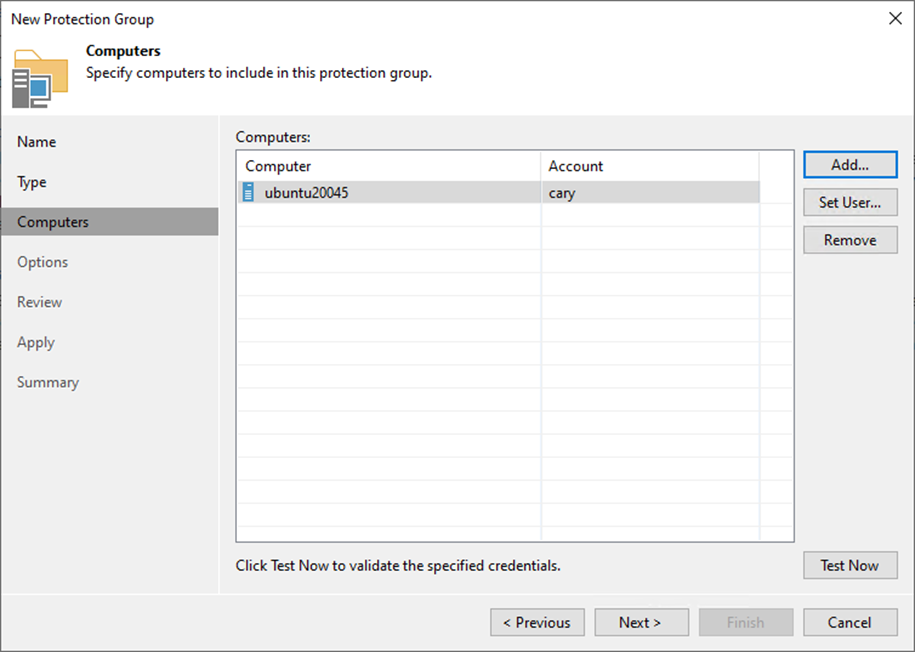
8. Click Add on the Computers page.
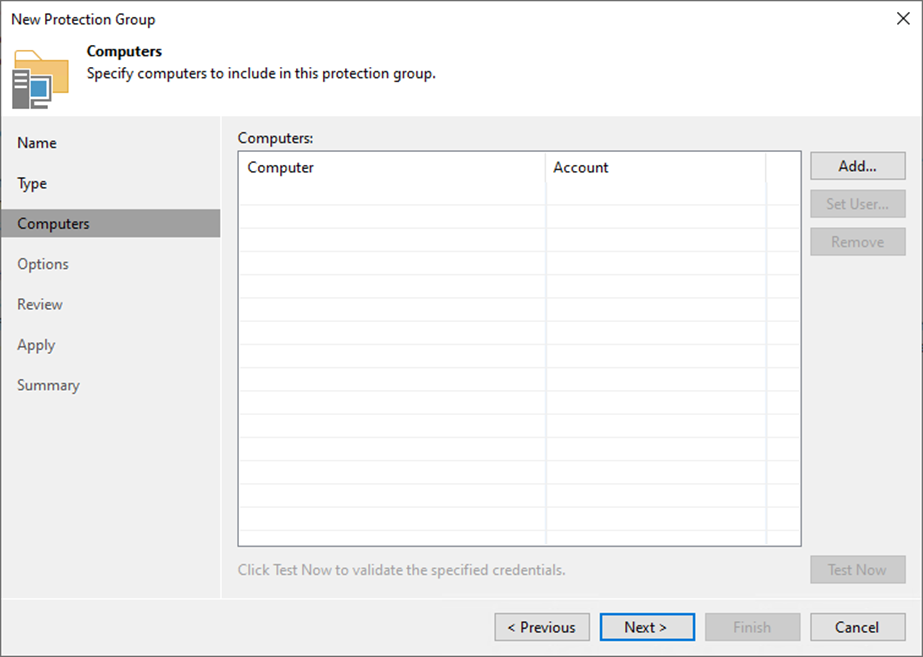
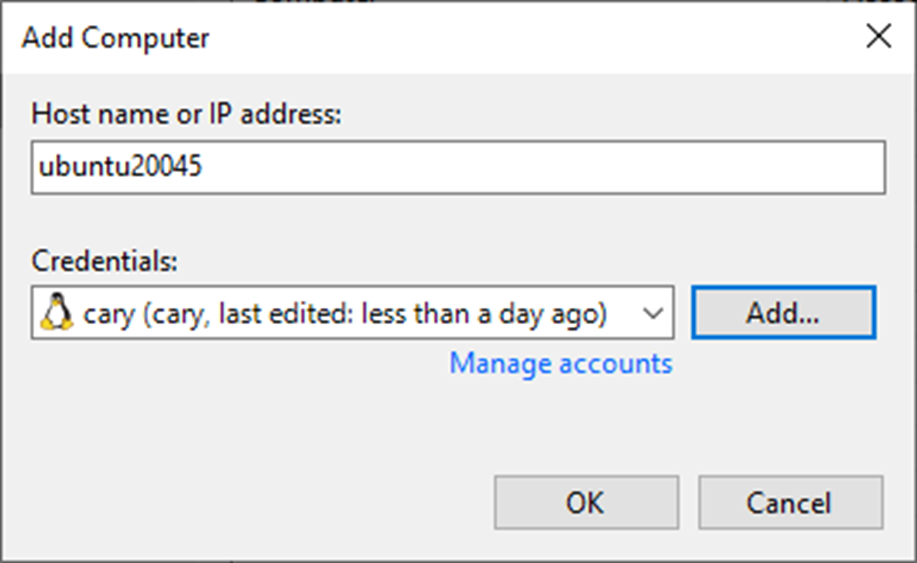
9. Specify a DNS name or IP address on the Add Computer page.
10. From the Credentials list, select a user account with administrative permissions on the computer and click OK.
11. If you need to set up credentials beforehand, click the Manage accounts link or Add on the right.
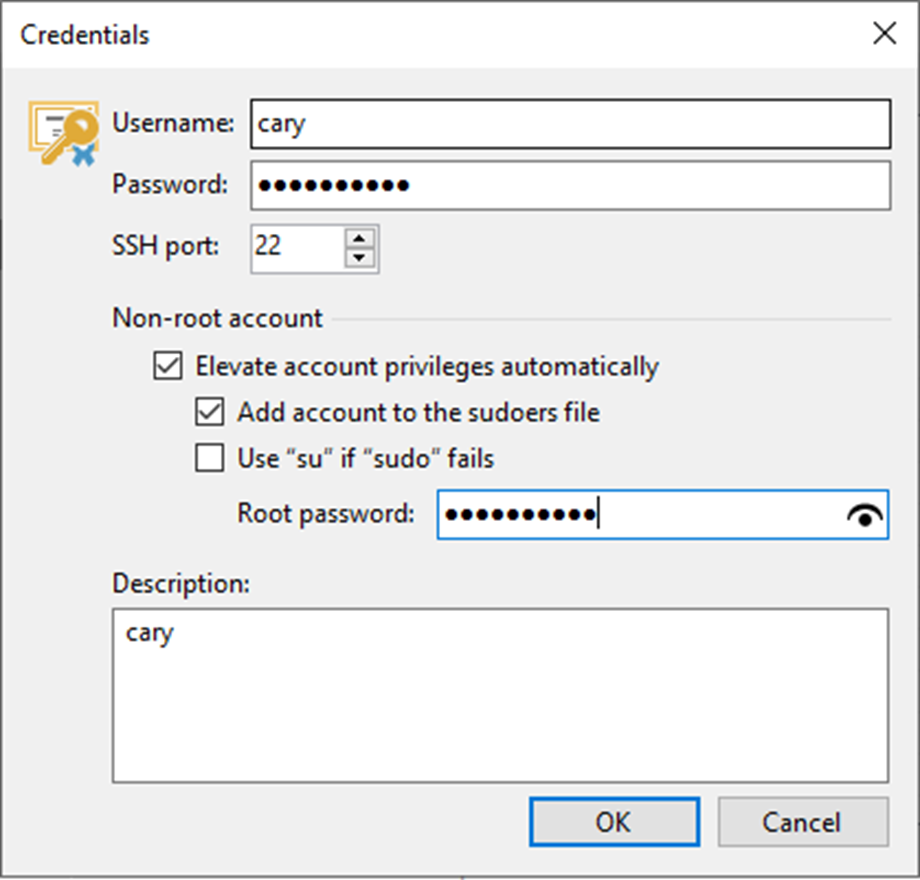
12. Click Add in the Credentials field, select Stored and click Linux account.
13. On the Credentials page, Enter a username in the Username field.
14. Enter a password in the Password field.
15. Enter 22 in the SSH port field.
16. Select the Elevate account privileges automatically checkbox for a non-root user with root account privileges.
17. Select Add account to the sudoers file checkbox.
18. Enter the password in the Root password field.
19. Give a brief description in the Description field for future reference and click OK.
20. Click OK on the add Computer page.
21. Click Test Now on the Computers page.
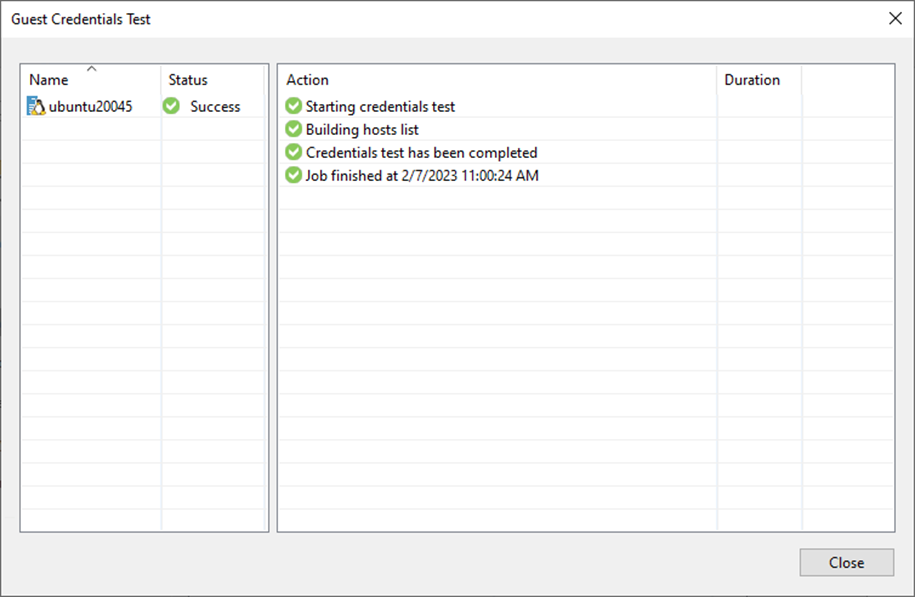
22. On the Guest Credentials Test page and click Close.
23. Click Next on the Computers page.
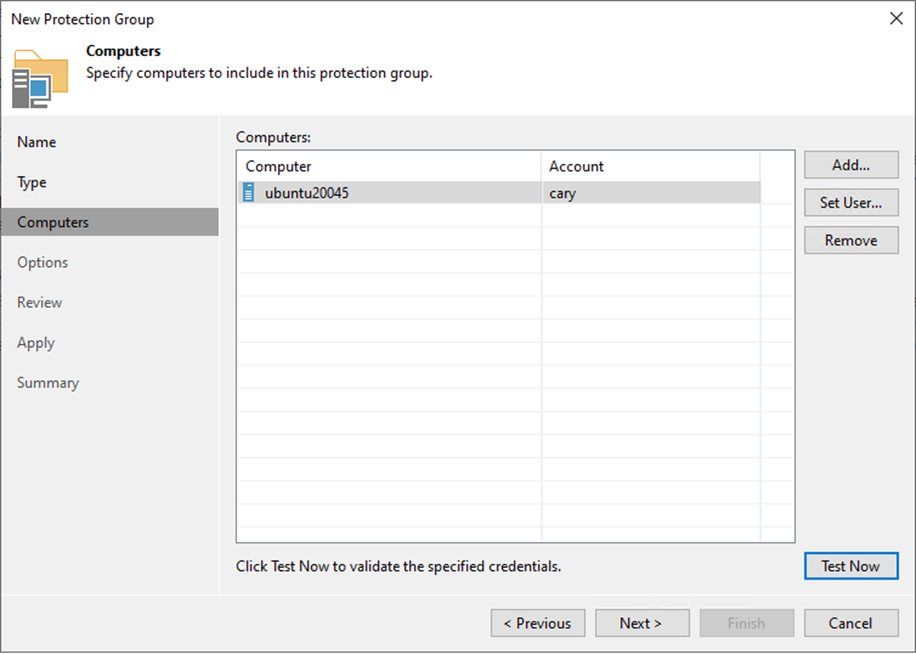
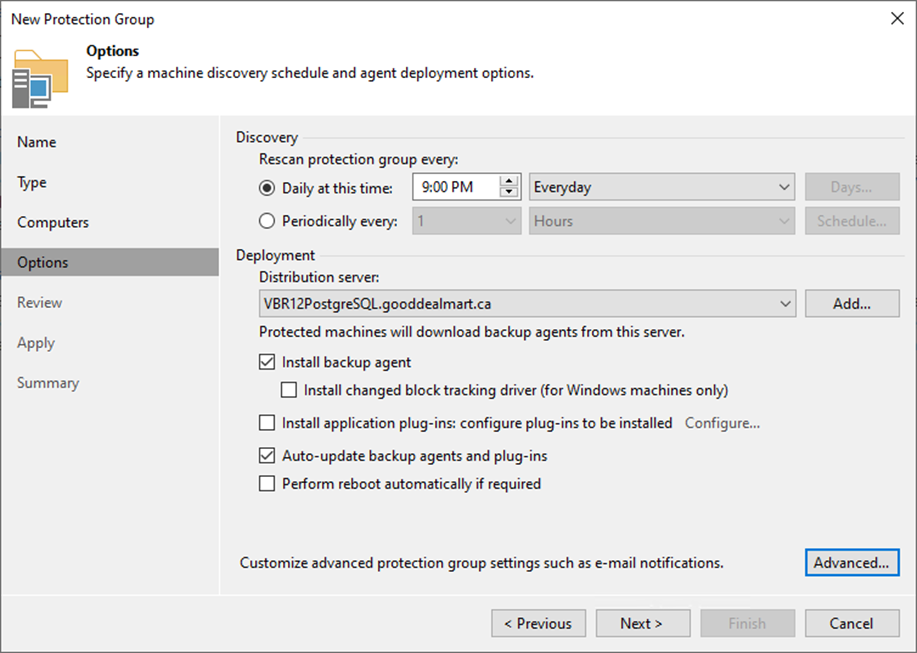
24. On the Options page, in the Discovery section, define the schedule for automatic computer discovery within the scope of the protection group.
25. In the Deployment section, select a Microsoft Windows server from the Distribution server list to serve as a distribution server.
26. Select the Install Backup agent checkbox.
27. Click Next to customize advanced protection group settings.
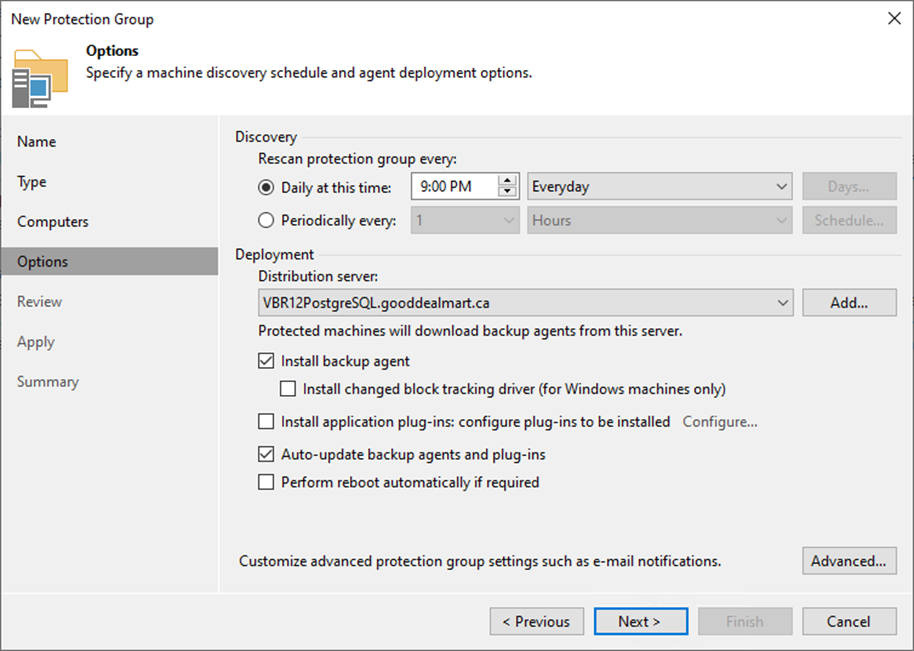
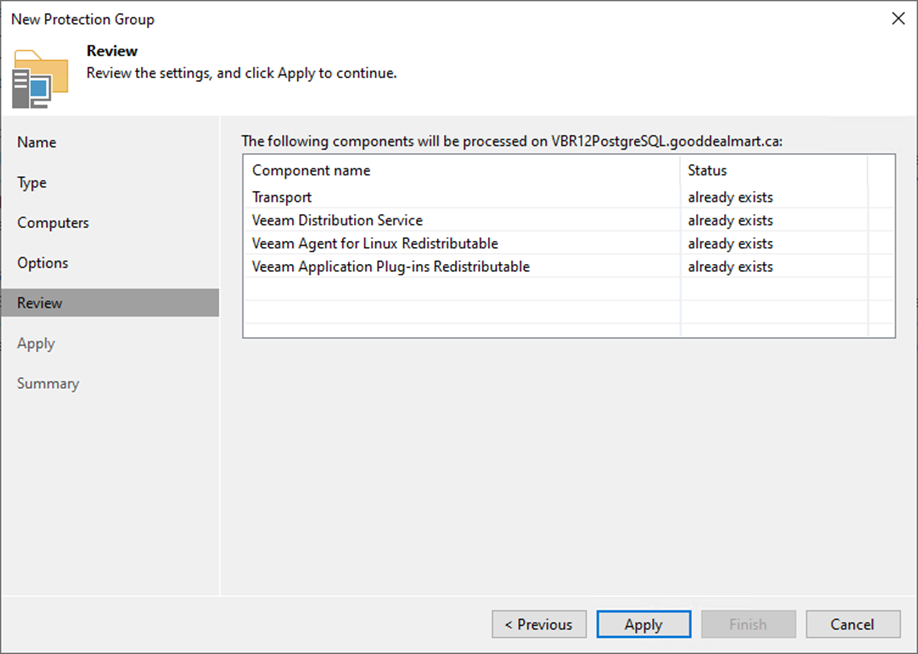
28. On the Advanced Settings page, specify the below settings that will be deployed on computers included in the protection group and click OK.
- Limiting bandwidth consumption: specify the maximum speed for transferring backed-up data from the Veeam Agent computer to the target location.
- Restrict metered connections usage: Veeam Agent automatically detects metered connections and does not perform backup when your computer is on such connection.
- Restrict VPN connection usage: Veeam Agent for Linux will automatically detect a VPN connection and not perform a backup when the Veeam Agent computer is on such a connection.
- Restrict Wi-Fi usage to these networks: restrict usage of wireless networks for Veeam Agent running on Linux.
29. Backup I/O settings: You can instruct Veeam Agent for Microsoft Windows to throttle its activities during backup.
- Throttle agent activity on the type of computers to throttle Veeam Agent backup activities: Workstations, Servers, or All hosts.
30. Security settings: You can allow user accounts that do not have administrative privileges on a Veeam Agent computer to perform a file-level restore on this computer.
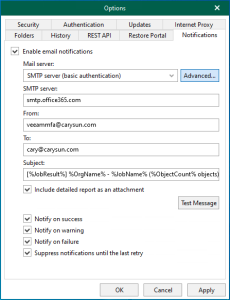
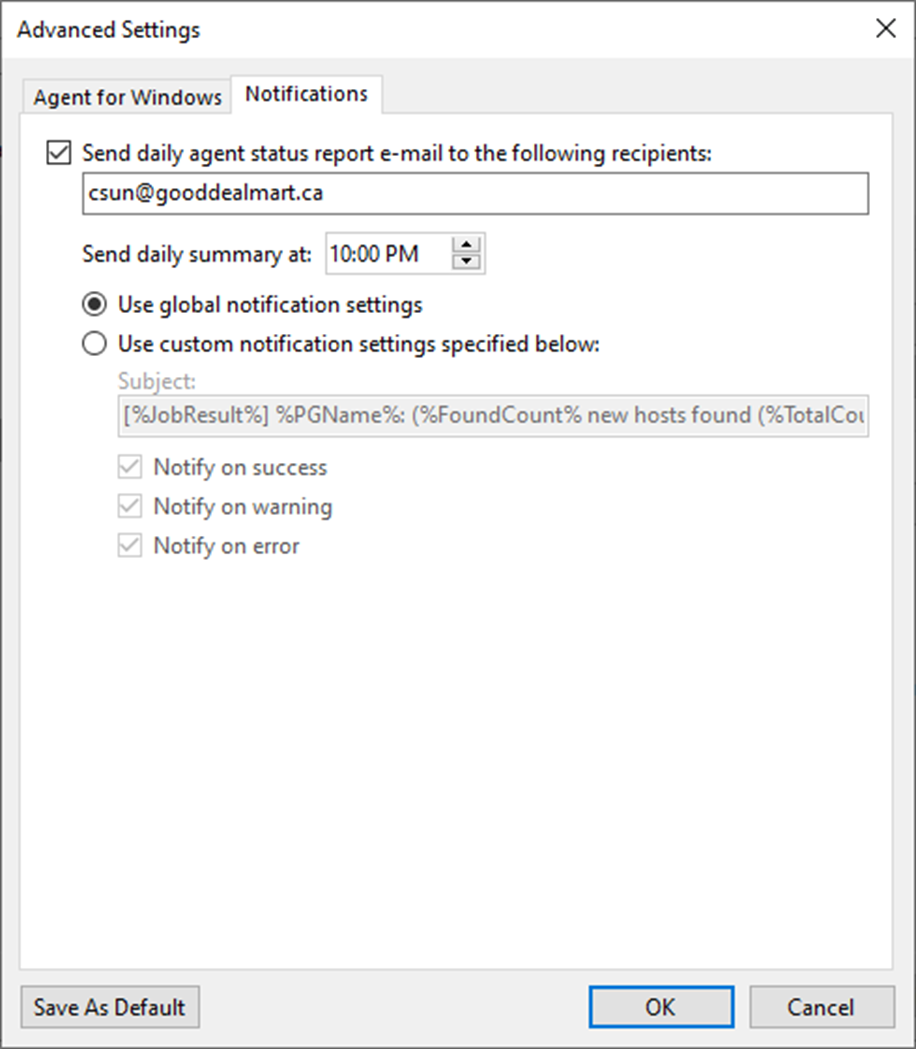
31. On the Advanced page, select Notifications.
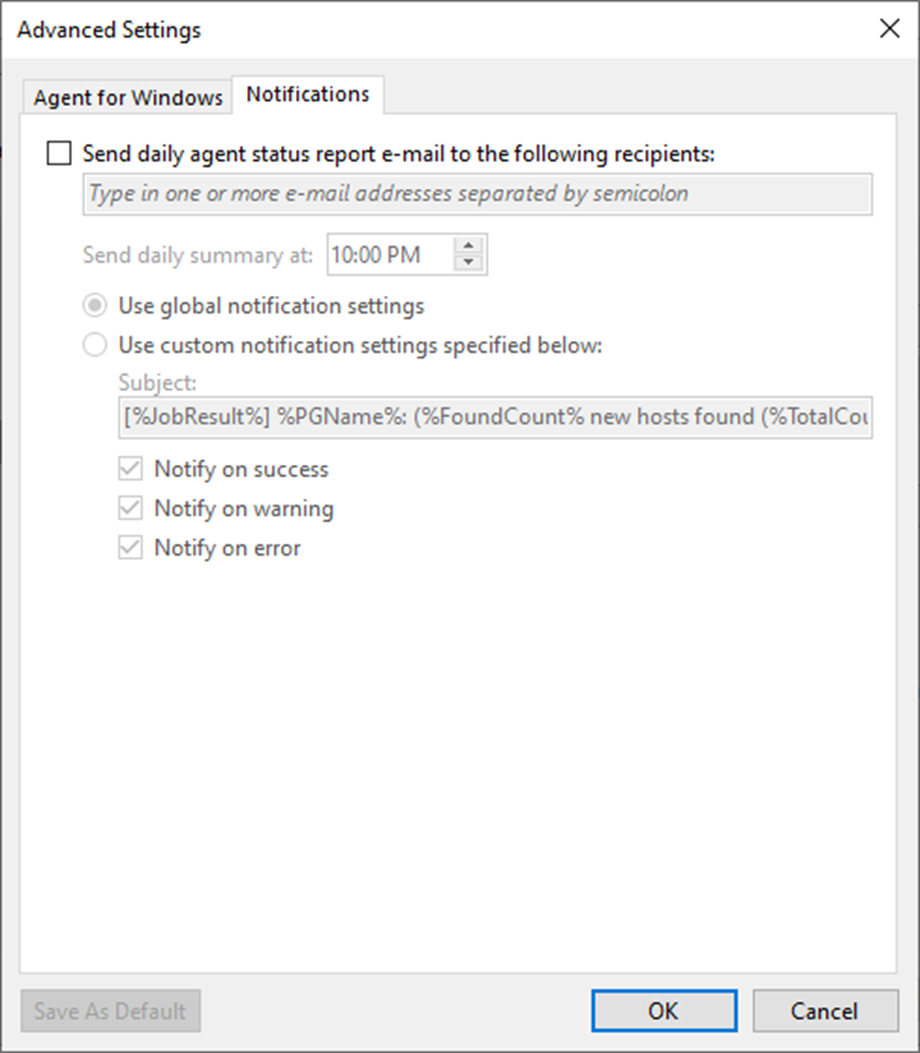
32. On the Notification page, select Send daily agent status report e-mail to the following recipients: checkbox and enter an email address.
33. Enter several addresses separated by a semicolon.
34. You can use global notification settings or specify custom notification settings and click OK.
35. On the Options page, click Next.
36. Click Apply on the Review page.

37. Click Next on the Apply page.
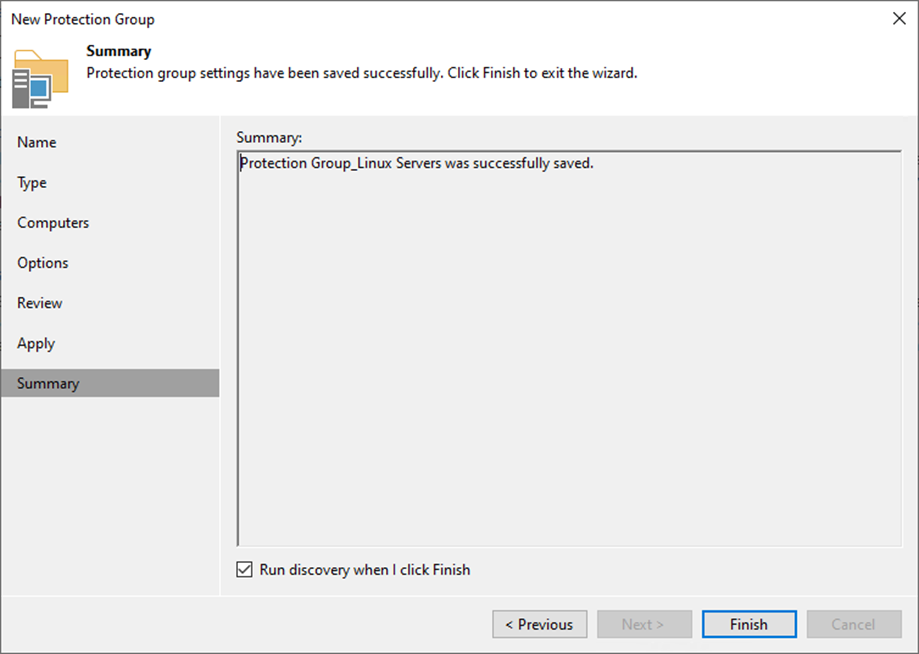
38. On the Summary page, select the Run discovery when I click Finish checkbox and click Finish.
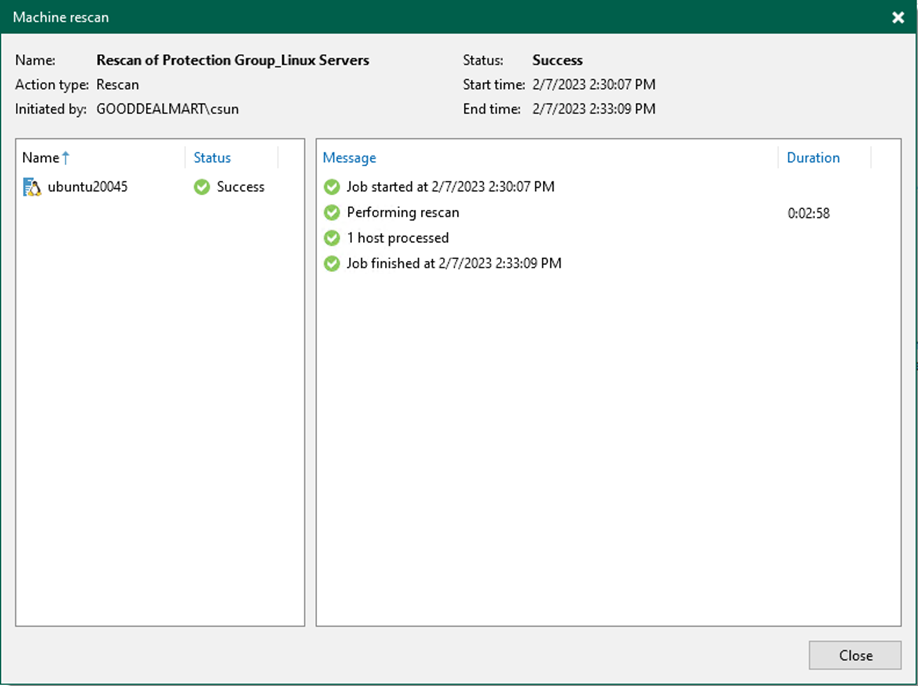
39. Verify the Machine rescan result and click Close.
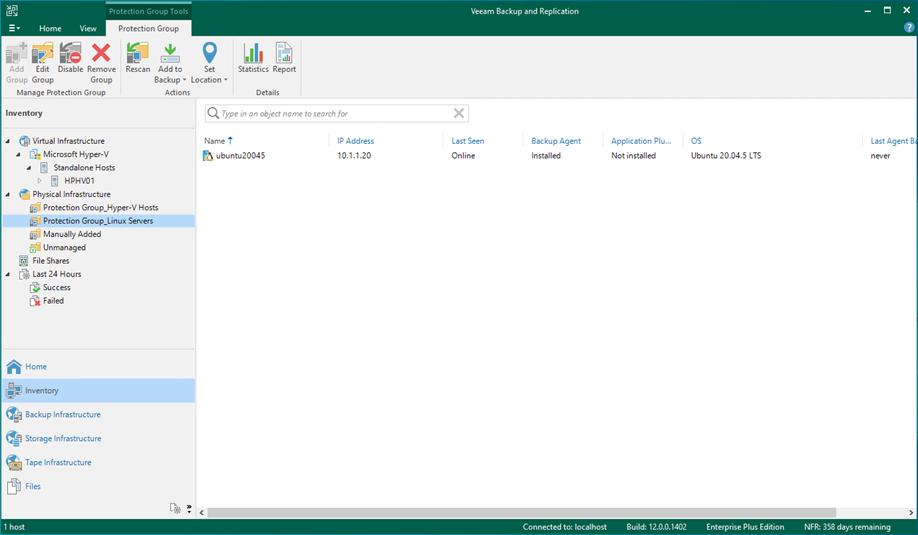
40. Verify that the protection group has been added.
I hope you enjoy this post.
Cary Sun
Twitter: @SifuSun
Web Site: carysun.com
Blog Site: checkyourlogs.net
Blog Site: gooddealmart.com
Author: Cary Sun
Cary Sun has a wealth of knowledge and expertise in data center and deployment solutions. As a Principal Consultant, he likely works closely with clients to help them design, implement, and manage their data center infrastructure and deployment strategies.
With his background in data center solutions, Cary Sun may have experience in server and storage virtualization, network design and optimization, backup and disaster recovery planning, and security and compliance management. He holds CISCO CERTIFIED INTERNETWORK EXPERT (CCIE No.4531) from 1999. Cary is also a Microsoft Most Valuable Professional (MVP), Microsoft Azure MVP, Veeam Vanguard and Cisco Champion. He is a published author with several titles, including blogs on Checkyourlogs.net, and the author of many books.
Cary is a very active blogger at checkyourlogs.net and is permanently available online for questions from the community. His passion for technology is contagious, improving everyone around him at what they do.
Blog site: https://www.checkyourlogs.net
Web site: https://carysun.com
Blog site: https://gooddealmart.com
Twitter: @SifuSun
in: https://www.linkedin.com/in/sifusun/
Amazon Author: https://Amazon.com/author/carysun